Stuxnet first and news of countless zero-day vulnerabilities in the wild have strengthened the idea that citizens security is constantly menaced by group of hackers that for different purposes are able to inflict serious damages to the structures that surround us.
Critical infrastructures represent privileged targets for very different actors such as cyber terrorists or foreign state-sponsored hackers, a heated debate is underway in the worldwide security community that is concerned about the cyber threats that need to mitigate in dire economic conditions and with limited budgets.
The security portal ThreatPost recently published the news related to new cyber attacks, malware-based, that hit two Power Plants using USB drivers as method of infection.
The events raised the needs to adopt, at corporate level, best practices for any security aspect included removable storage, a critical issue for security of control system inside critical infrastructures.
According a report from the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), three instance of malware were discovered fortuitously after a scan of an USB drive used to back up control systems configurations. One of the instances detected is considered very sophisticated, increasing the level of alert on the event.
Further analysis revealed other absurd security flaw, for example it was absent a backup management for critical workstations inside the plant.
“The organization also identified during the course of the investigation that it had no backups for the two engineering workstations. Those workstations were vital to the facility operation and, if lost, damaged, or inoperable, could have a significant operational impact. The recommended practice is to maintain a system of ‘hot spares’ or other effective backups for all critical systems.”
The main problem is that majority of control systems are privately owned, and leak of investment in security advantages the work of hackers. Elementary security measures could sensibly improve security level of infrastructures, let’s think to the establishment of proper defensive measures of the correct configuration of any devices exposed in internet.
The report states:
“While the implementation of an antivirus solution presents some challenges in a control system environment, it could have been effective in identifying both the common and the sophisticated malware discovered on the USB drive and the engineering workstations,”
Similar incidents are not rare, in October, ISC-CERT reported the infection of 10 computers linked to another power company’s turbine always via a USB drive…and the list is long.
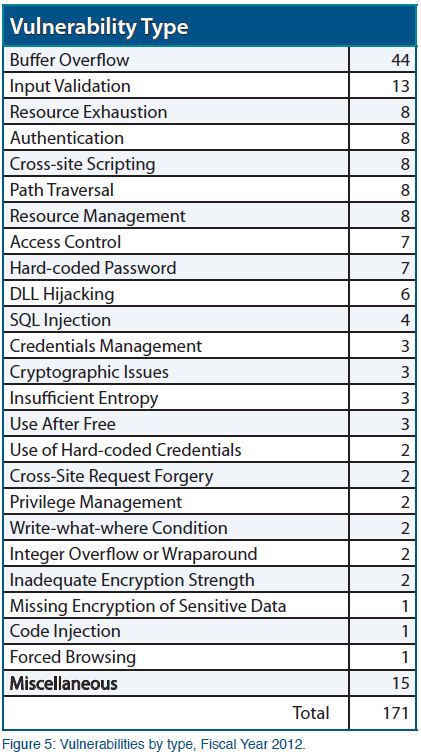
Summarizing the vulnerability analysis proposed by ICS-CERT :
“in fiscal year 2012, ICS-CERT tracked 171 unique vulnerabilities affecting ICS products. ICS-CERT coordinated the vulnerabilities with 55 different vendors. The total number of different vulnerabilities increased from FY 2011 to FY 2012, but buffer overflows still remained as the most common vulnerability type”
Besides the security aspect, as I mentioned before, it’s necessary to evaluate the financial prospective of cyber security market in the defense sector.
Cyber strategy of any state puts the security of critical infrastructures at the topmost priority, in particular for the global oil and gas industry also in response to recent series of attacks. An analysis from Frost & Sullivan revealed that the market earned revenues of $18.31 billion in 2011 and estimates this to reach $31.27 billion in 2021. The investments are driven by the growth of the sector and related need of physical and cyber security.
Anshul Sharma, Senior Research Analyst at Frost & Sullivan Aerospace, Defence & Security, declared:
“Global oil and gas companies are investing capital in new infrastructure projects, driving the need for security solutions at these facilities,” “With increasing awareness of threats, companies are adopting a security-risk management approach and implementing risk assessment of their facilities to ensure security Return on Investment (ROI).” “The threats may vary from information theft to a terrorist attack, but the economic impact and financial damage in case of an attack will be much more significant,” “It would also depend on the motive of the attacker. For example, a cyber attack to remotely control a SCADA system can have more serious consequences than a cyber attack to steal information.”
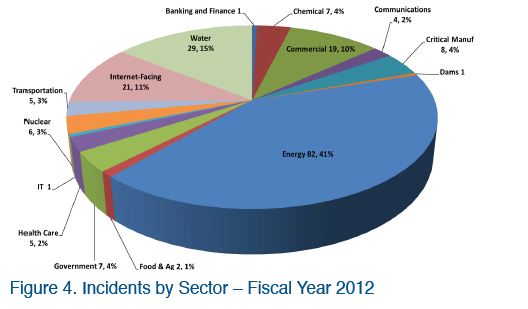
It’s clear that new opportunities for cyber security experts will be created in the incoming years, probably something is changing the mind of top manager that are driving the companies of the sector is a profitable business.

It's an interesting article, I've personally seen hackers in a malicious light. I do know there are people who hack for nefarious needs, I just haven't really experienced it too much myself.
ReplyDeleteI do believe that most security breaches via hacks are usually due to negligence by the company. But regardless, no matter how flawless your systems are- someone will always find a way through it.
Wow, amazing
ReplyDelete