
Many be many of you are not aware about this, but Facebook having a Secure Files Transfer service for their Employees athttps://files.fb.com and Hacker reported a very critical password reset vulnerability.
Nir Goldshlager, a researcher told 'The Hacker News' that how he defeat Facebook's Secure Files Transfer service and help Facebook by reporting them about this issue in a responsible non-disclosure way till patch.
After analyzing the site, he found that the script Facebook is using is actually "Accellion Secure File Sharing Service" script and so next he download the demo version of service from Accellion website and explore the source codes and file locations.
Nir Goldshlager, a researcher told 'The Hacker News' that how he defeat Facebook's Secure Files Transfer service and help Facebook by reporting them about this issue in a responsible non-disclosure way till patch.
After analyzing the site, he found that the script Facebook is using is actually "Accellion Secure File Sharing Service" script and so next he download the demo version of service from Accellion website and explore the source codes and file locations.
He found that, there is a user registration page also available in source, that was also on files.fb.com. Unfortunately Facebook had removed the Sign up option (link) from homepage, but forget to remove the registration page from its actual location i.e (/courier/web/1000@/wmReg.html).
So this way, Goldshlager was able to make an account on the site for further pentest. He found that the demo source code of the service is encrypted by ionCube PHP Encoder, and decryption of many parts of the source code was not possible by him.
Source code of a web application is like a treasure for a penetration tester, once you have source code, you can look for many critical web application vulnerabilities easily. Anyway, he drop that idea because source code is encrypted.
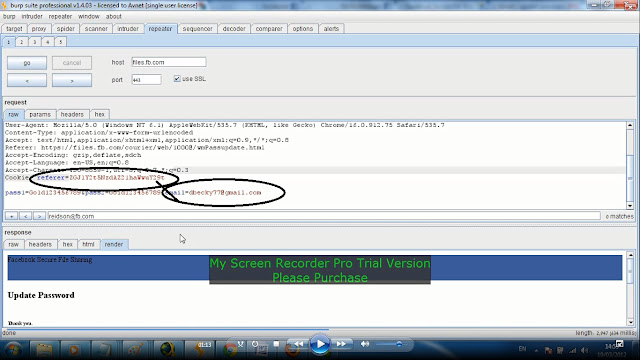
There is a Password Recovery page (wmPassupdate.html) also available on site, which was actually allowing anyone to reset the passwords of any account. Goldshlager notice that when one request to reset the password of his account, the page was validating the user by a cookie called "referer" that contained the email ID of same logged in user but encrypted in Base64.
Finally, Goldshlager hack the Facebook Employees Secure Files Transfer service by tampering the values of cookies equals to the victim email ID and Password parameters. This way he was able to reset the password of Facebook Employees using this critical flaw. Flaw was reported by him and now patched by Facebook.
So this way, Goldshlager was able to make an account on the site for further pentest. He found that the demo source code of the service is encrypted by ionCube PHP Encoder, and decryption of many parts of the source code was not possible by him.
Source code of a web application is like a treasure for a penetration tester, once you have source code, you can look for many critical web application vulnerabilities easily. Anyway, he drop that idea because source code is encrypted.
There is a Password Recovery page (wmPassupdate.html) also available on site, which was actually allowing anyone to reset the passwords of any account. Goldshlager notice that when one request to reset the password of his account, the page was validating the user by a cookie called "referer" that contained the email ID of same logged in user but encrypted in Base64.
Finally, Goldshlager hack the Facebook Employees Secure Files Transfer service by tampering the values of cookies equals to the victim email ID and Password parameters. This way he was able to reset the password of Facebook Employees using this critical flaw. Flaw was reported by him and now patched by Facebook.
source: thehackernews.com

I hope facebook paid him for bringing this vulnerability to their attention
ReplyDeleteWow, that makes the usage of Facebook even more dangerous than it already is. Glad you shared this, really interesting facts there!
ReplyDelete