It’s not a mystery, every state despite the spending review on the military budget is continuing to reserve consistent investment in cyber security, in particular majority of states is pushing research and development activities on both defense and offense cyber capabilities.
US is one of the most advanced country in cyber warfare, the US Government was one of the first to recognize the importance of operations in the cyberspace and the necessity to consider it as the fifth domain of warfare.
Since now the estimations on US expenses in cyber operations were estimates of the leading experts in the field but for the first time The Pentagon has detailed $30 million in spending on Air Force cyber attack operations and new Army funding.
With the public disclosure of the budget for cyber operations US, in particular the Defense Department, desires to provide to national taxpayer’s evidence of effort spent in what is being considered a critical component of the modern military.
The public opinion is dedicating even more wide space to news related cyber security and to the risks related to a cyber attack against critical infrastructures of a country, the government with the announcement desire to inform his population on its network assault programs and of course to launch a warning to those who intend to attack the country from cyber space.
The Pentagon revealed the intent to constitute and fund new staff dedicated to offensive cyber operations for the exploitation of opponent networks and infrastructures.
This week is circulated the document titled “Fiscal Year (FY) 2014 Budget Estimates – OPERATION AND MAINTENANCE, AIR FORCE” to explain how US intends to invest the money, lets’ go to analyze in detail the amount of money reserved by the US Administration.
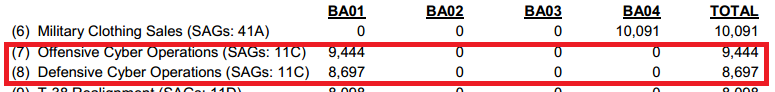
The Air Force in fiscal 2014 will reserve $19.7 million on “offensive cyber operations,” the expense will support operative cyber operations, personnel training and research and development activities. In cyber warfare scenario a crucial role is played by cyber tools used to exploit opponent’s structures so US estimate needing $9.8 million for development of new cyber tools to use in cyber operations.
The Pentagon proposed also the hiring of new personnel, 65 units, to dedicate to the cyber missions, the mission assigned to Cyber Command is critical because it is responsible to deflect incoming assaults from cyber space against critical infrastructures of the country.
Of course part of the funds will be dedicated to Defense Cyber Operations to protect data and infrastructures of the country from cyber attacks, sabotage and cyber espionage.
Following a portion of the “Summary of funding Increases and Decreases” related to the “cyber commitment”:
Transfers In
Transfers Out
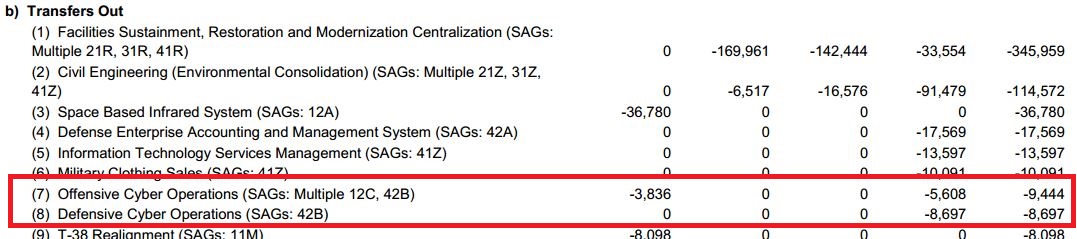
Nextgov portal reported the US government chose to divulge this information “because cyber offense will be a standard line item from now on and the public needs to understand what it is paying for.”
To those taxpayers that as justification for the investments in cyberspace while defense budget is under cutting Air Force spokesman Maj. Eric Badger replied:
“We are committed to maintaining the right balance of integrated cyber capabilities and forces that are organized, equipped and trained to successfully conduct operations in cyberspace. We’re equally as committed to doing so in a way that’s respectful of the taxpayers’ dollar,”
“We know the Air Force’s capabilities in cyber are going to continue to be touchstones for the whole joint team, the whole of government and for the private sector,” the official added.
According Nextgov further $4.9 million will be dedicated to the development of “computer network exploitation” and “computer network attack” capabilities.
Of course no shortage of controversy for military spending, analysts accused the government of excessive and duplicated hacking investments. Todd Harrison, senior fellow for defense budget studies at the Center for Strategic and Budgetary Assessments accuses the dispersion in cyber attack spending to fund different commands within US army:
“Do we really want each service going off and developing their own capabilities for these threats?” questioned “How much redundancy are we building across the services in the areas of cyber? What is unique to the Army?” “Maybe it’s time to give Cyber Command more budget authority,” Harrison said.
Other military experts said the services might be giving away these details to ward off potential foes on the Internet.
I will not go into the merits of the distribution of spending and allocation of responsibilities for operations in cyberspace, but I believe that investment in cyber security is crucial for the cyber strategy of each country … Probably the funds allocated are still too small compared to the need for cyber security.
source: http://securityaffairs.co
